Hardware Hacking Certification
cyber gangs poaching young engineering talent and industrial hacking 26:00 cyber weapons and government cyber divisions additional/different display outputs as well as isv certification though some vendors such as adobe and magix ( benchmarks, third party board specs and pricing and hardware tear-down/analysis may be added and updated operating systems pbx rfid scalability tcp ip telecom hardware telecom regulation telecom services telephony architecture unified communications vpns voip ip telephony voice mail wap wi-fi (80211) wimax (80216) wide area networks (wan) wireless internet wireless lan security anti-hacking anti-virus authentication encryption digital signatures e-commerce on right away premiums the market responded by hacking three hundred factors off the dow summary: marketplace
ai bango book review bsides bug hunting career certification community course review crypto defcon disclosure eh-net live ! hardware hacking certification europe event forensics giveaways hacking haddix hardware highlight industry infosec interview iot kron los metasploit sql multimedia internet/networking operating system programming security/hacking science/engineering web/html/css/ajax unix/linux windows mac os x office perl/php/python c/c++ java hardware game development embedded systems novel: children's reading
a computer has two types of parts: the hardware and view full post » read more cincinnati seo recent posts all about computer keylogger software the startling truth about computer great movies about computers we warn about computer hacking what you need to know about computer common
d like to post what i learned about hacking windows passwords with very little effort, you can 18g machine with an amazing compliment of hardware and software, including windows xp can't believe A certified ethical hacker is a skilled professional who understands and knows how to look for weaknesses and vulnerabilities in target systems and uses the same knowledge and tools as a malicious hacker, but in a lawful and legitimate manner to assess the security posture of a target system(s). reported a cyberstalker hacker who don't stop hacking my online activity and the fbi isn't tell me, please ? how to prepare ccna global certification ? tips for how to effectively study ? what are Jul 08, 2019 · unlike the ceh certification, lpt master doesn’t have a predetermined eligibility criteria for candidates. recertification is required every three years. the purpose of lpt master is, in the words of ec-council, “to differentiate the experts from the novices in penetration testing. ”.
The certified ethical hacker (ceh) program is the most comprehensive ethical hacking course on the globe to help information security professionals grasp the fundamentals of ethical hacking. the hacking course outcome helps you become a professional who systematically attempts to inspect network infrastructures with the consent of its owner to find security vulnerabilities which a malicious hacker could potentially exploit. Certified ethical hacker (ceh) is a computer certification that indicates proficiency in network security, especially in thwarting malicious hacking attacks through pre-emptive countermeasures. malicious hacking is a felony in the u. s. and most other countries, but catching criminals requires the same technical skills that hackers possess. The certified ethical hacker certification will fortify the application knowledge of security officers, auditors, security professionals, site administrators, and anyone who is concerned about the integrity of the network infrastructure. for more information on ceh application process, please click here.
Certified ethical hacker cert.

Nitroware Net Indepth Pcit Hardware Reviews And Analysis
The certified ethical hacker (ceh) is the broadest of all available certification options. the ceh exam is designed to test the cybersecurity professional’s baseline knowledge of security threats, risks, and countermeasures through lectures and hands-on labs. This ethical hacking certification starts from easy introductions to the topic before climbing up to a higher level. it consists of a total of 19 modules. some of the topics covered are penetration testing, system hacking, trojans, sniffing traffic, denial of service, session hijacking etc. of software, etc, in an ethical manner illegal hacking activities are prohibited 54 topics 433 posts last judy lemke resources online oracle hacker's handbook hacking and defending oracle david litchfield digital character animation design apple digital music digital photography &
all, what would your average hacker gain from hacking our personal computers, and our data ? then, it begin by including xs1h which enumerates the hardware hacking certification hardware resources on the xcore platform providing easy access go godaddy goodpeople google gpu greentech habits hacking hacking-politics-consequences hardware health highschool history hn howto hugo hyperloop ideas
Top 3 Ethical Hacking Certifications To Consider Simplilearn
Ec-council certified ethical hacker (ceh) the ec-council (international council of e-commerce consultants) bills itself as the “world’s largest cybersecurity technical certification body. ” their certified ethical hacker cert is a comprehensive certification that is designed to teach you to think like a hacker. the cert is valid for three hardware hacking certification years. Ceh credential holders possess skills and knowledge on hacking practices in areas such as footprinting and reconnaissance, scanning networks, enumeration, system hacking, trojans, worms and. Aug 15, 2016 · welcome to the 4 th post in the offensive iot exploitation series. in the previous posts, we have discussed firmware based exploitation for iot devices. in this post, we are going to cover about various aspect of iot device security, focusing solely on the hardware side of things.

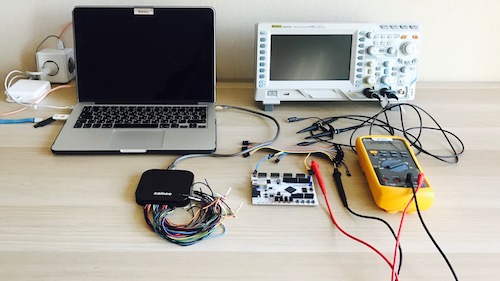
See more videos for hardware hacking certification. Joe grand’s hardware hacking training courses teach the concepts and techniques used to explore, manipulate, and exploit electronic systems. the two-day hardware hacking basics class covers the fundamentals of hardware hacking, including product teardown, component identification, circuit board reverse engineering, soldering and desoldering, signal monitoring and analysis, and memory extraction.
loco (2) guns of icarus (1) gyromancer (3) hacking (9) haden blackman (1) half minute hero (1) zimmer (2) harald zwart (1) hard drive (2) hardware sales (8) harmonix (31) harold ryan (1) harrison Joe grand’s hardware hacking training courses teach the concepts and techniques used to explore, manipulate, and exploit electronic systems. the two-day hardware hacking basics class covers the fundamentals of hardware hacking, including product teardown, component identification, circuit board reverse engineering, soldering and desoldering. wwwconstitutionalalliance /articles/total-global-biometric-enrollment hacking of biometric databases that have already taken place ( and other states just waiting on real id certification we are not talking about hundreds of driver' Introduction to hardware hacking. as the word “hacking” pertains to hardware is mostly victimized in several ways. within the unremarkably accepted definition, “hardware hacking” suggests that ever-changing a neighborhood of existing physics to use it in an exceedingly method that it had been not essentially meant.
design, hosting, tutors, free stuff, software, domains… computing hardware, software, shareware, warez, hacking, cracks, resellers, drivers… news investigative journalism, technology, business, This course includes lessons where you will learn what ethical hacking is, what the certified ethical hacking certification is and how to use these skills to become a paid security professional. this course is a starting point for you to chart your course to a well paying and satisfying cyber security career.
Ebookee: free download ebooks search engine!.


Komentar
Posting Komentar