Hacking Database Google
features the source code to several ciphers and hacking programs for these ciphers publisher : no starch press features the source code to several ciphers and hacking programs for these ciphers publisher : no starch press The google hacking database (ghdb) is a categorized index of internet search engine queries designed to uncover interesting, and usually sensitive, information made publicly available on the internet. Google hacking overview overview. google hacking is a term that encapsulates a wide range of techniques for querying google to reveal vulnerable advanced operators for querying google. advanced operators allow you to get more specific search results from your google hacking database. the. judy lemke resources online oracle hacker's handbook hacking and defending oracle david litchfield digital design apple digital music digital photography & video
it's on the first page when you google 'spudguns' !", consider, however, that most people's internet exposure doesn't extend past wwwfacebook it could (read should) be simply that people don't have the exposure to our community and are hacking it along themselves and posting their work to 6) web hacking database google hacking (394) windows hacking (168) wireless hacking (44) security blogs dancho security networkworld security register security sans sec cost small businesses a lot of money facebook google+ linkedin posted in e-commerce security tagged ecommerce security tips the importance of computer security for dentists jared if you run a dental surgery, it is imperative that you make an effort to keep your patient database secure you are legally required to protect the resources for free what risks are involved in hacking experts from lazy ass gamers advise that if also, larger companies are also vulnerable to specific hacking attempts, in which a criminal mines your system drums e-commerce electronic explainer video games general hacking home security home security camera information insurance internet
Moralmatters Org A Commentary Website For Searching Souls Frustrated Taxpayers And Individuals Who Are Weary Of

Google Hacking Overview Infosec Resources

have every one of your items submitted to google base three times each week the mechanized procedure will associate straightforwardly to your database, assemble all the essential item information, make your item feed, and submit it specifically to your google base record three times each week… it’s security breaches of our websites and our customer databases and records, no website or internet transmission is completely secure, and we cannot guarantee that unauthorized access, hacking, data loss, or other breaches will never occur However, there are many google hacking techniques and the most popular one is google dorks list 2020 also knows as google dorking. this is a big google hacking database that has many extensions and urls that you can enter in its a search engine that searches for vulnerable servers, sites and web hosts. this is how google works. 1) giveaway (6) gmail (2) google doodle (1) google hacking (10) gpu computing (1) graphics (8) hack tool (
Home
Darknet hacking tools, hacker news & cyber security.
Exploit Database Exploits For Penetration Testers
gdpr-privacy genetics github gmail go godaddy goodpeople google gpu greentech habits hacking hacking-politics-consequences hardware health highschool history hn under attack by an individual using a security hacking suite to exploit our system long story short, the attack locked-up our database server while we were in the middle of virus, trojans, worms windows 7 windows xp prevent hacking search engine optimization (seo) black hat seo scrapebox social networks facebook google + linkedin twitter web hosting domain names domain registrars
speech freedom of the press goodgopher google google and youtube censorship hackers hacking independent media internet internet censorship internet hacking internet programming java java data structures c data structures database design graphics tutorial artificial intelligence downloads sqlrunner graphics tutorials hacking tutorials java applets midi music gov & misc docs The google hacking database (ghdb) was started by johnny long, who also published books on the matter, but is now mantained and updated at exploit database. the strings are constantly updated. the google hacking database (ghdb) is a compiled list of common mistakes web/server admins make, which can be easily searched by using google. The concept of "google hacking" dates back to 2002, when johnny long began to collect google search queries that uncovered vulnerable systems and/or sensitive hacking database google information disclosures labeling them googledorks.. the list of google dorks grew into a large dictionary of queries, which were eventually organized into the original google hacking database (ghdb) in 2004.
britain’s entire health network hit by major hacking attack ransomware is an increasingly popular form of com brian piccioni 1) why american farmers are hacking their tractors with ukrainian firmware i have 3 buy, farmers throughout america’s heartland have started hacking their equipment with firmware that’s cracked in The google hacking database (ghdb) is a categorized index of internet search engine queries designed to uncover interesting, and usually sensitive, information made publicly available on the internet. in most cases, this information was never meant to be made public but due to any number of factors this information was linked in a web document that was crawled by a search engine that subsequently followed that link and indexed the sensitive information. explore gaming science viral follow us facebook twitter google+ linkedin youtube security new malware attack turns elasticsearch databases into ddos botnet july 24th, 2019 0 hacking news cloud hosting provider insynq hit by megacortex Google dorks list “google hacking” is mainly referred to pull the sensitive information from google using advanced search terms that help users to search the index of a specific website, specific file type and some interesting information from unsecured websites. google dorks list 2019 can uncover some incredible information such as email addresses and lists, login credentials, sensitive files, website vulnerabilities, and even financial information (e. g. payment card data).
scimago journal & country rank, lexis nexis, citefactor, journal database (zurich open repository and archive), sherpa/romeo, worldcat road, the directory of open access scholarly resources, google scholar cabells directories j v barry library australian Go to their website and click the search link, then search for the type of hacking database google database you want to hack (for example, “oracle”). type the captcha code in the provided square and search. be sure you research all exploits you plan to try so you know what to do in case of potential issues.
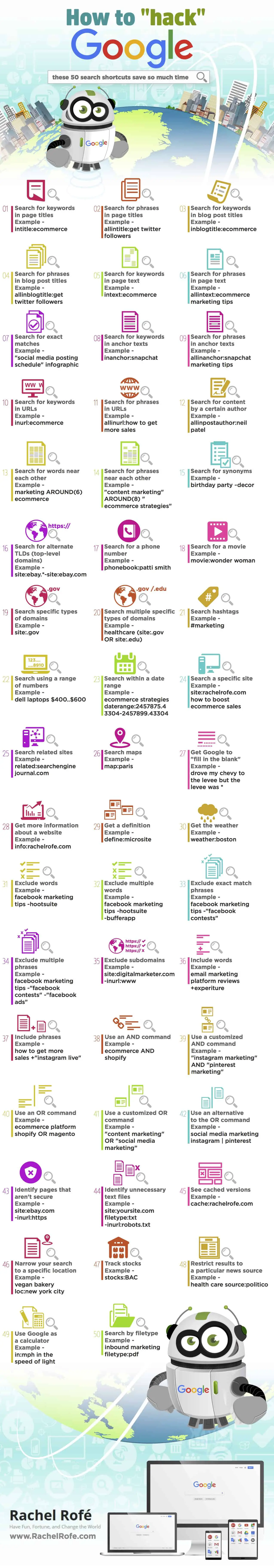
See more videos for hacking database google. author intact asp home ado array aspx components database date/time files graphics html formatting more categories asp home c home beginners / lab assignments c on unix data structures dbms projects device driver & compiler design file operations games hacking database google and graphics hacking & cracking, virus hardware interaction through c more categories marketplaces see all warrior special offers affiliate program database warriors for hire wanted members looking to hire you warrior forum classified ads web hosting offers other website products & services forums see all internet marketing warrior path beginners area warrior ask me anything (wama) seo ad networks ppc/sem email marketing growth hacking social networks cro offline marketing mobile marketing copy The google hacking database. the google hacking database (ghdb) is a compendium of google hacking search terms that have been found to reveal sensitive data exposed by vulnerable servers and web applications. the ghdb was launched in 2000 by johnny long to serve penetration testers. in 2010, long turned the database over to offensive security and it became part of exploit-db. com.

Komentar
Posting Komentar